TrueCrypt volumes
Summary
- Hash algorithms used: RIPEMD-160, SHA-512, Whirlpool
- Encryption algorithms used: AES, Twofish, Serpent
- Complexity of attack: Very high to impossible
- Password recovery speed (RIPEMD-160, SHA-512): thousands (CPUs), tens of thousands (GPUs)
- Password recovery speed (Whirlpool): hundreds (CPUs), thousands (GPUs)
- CPU optimizations: generic x86/x64 code, SSE2, AVX, XOP, AVX2
- NVIDIA GPUs support: Fermi/Kepler/Maxwell/Pascal (GeForce GTX 4xx-1080)
- AMD GPUs support: RV710+ (HD4350 to R9 295X2)
General information
TrueCrypt software was designed to provide high level of protection and it stays true in reality. Generally speaking it's impossible to crack TrueCrypt volumes without additional knowledge about password used. Or if password was ridiculously weak but it's very unlikely that somebody was paranoid enough to use TrueCrypt but chose weak password.
Current version limitations
- Only XTS encryption mode is supported.
- Key file(s) are not supported.
Attack settings
TrueCrypt volumes doesn't store any information unencrypted. In fact it's even impossible to detect is given file a TrueCrypt volume or not — there no signatures inside. Due to their nature encrypted volumes are usually large and high entropy files but there no guarantee at all.
As it's impossible to recognize TrueCrypt volumes by file content you're need to use File/Open As ... menu command and explicitly mark file as TrueCrypt container one.
Thus, user must provide additional information to reduce complexity of attack. TrueCrypt settings dialog looks like:
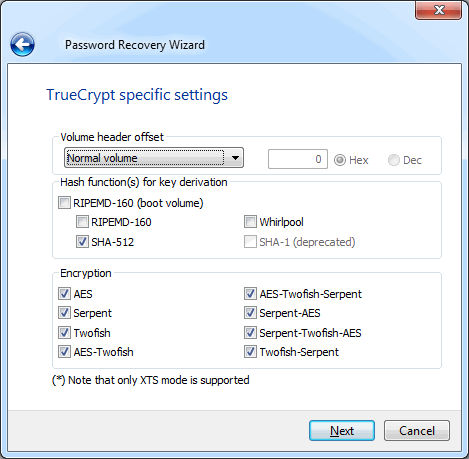
Note that current version of this software does not support deprecated protection schemes used by TrueCrypt (like SHA-1 based key derivation or LRW encryption mode).
To start attack you must select at least:
- Volume header offset — it's zero for standard volumes, only 512 bytes required for attack;
- Key derivation functions used — select all applicable options;
- Encryptions used — select all applicable options.
Note that each separate encryption requires additional set of keys and so key derivation function will need to produce more output making the whole process slower. For example, schemes with single algorithm (i.e. AES or Twofish or Serpent) requires only 64 bytes of output while complex schemes (like AES-Twofish-Serpent) requires 3x more = 192 bytes of output. As key derivation function is a main source of all computations required it effectively means that complex schemes with 3 algorithms will be checked 3 times slower than single ones.
Generally speaking, if you've selected AES-Twofish-Serpent or Serpent-Twofish-AES there no point to uncheck any other encryption options. From the other side, if you're absolutely sure that only AES used you can uncheck all 2 and 3-way schemes increasing password search rate triple times (and, just in case, you can keep single Twofish and Serpent checked as well without noticeable performance drop).
Obviously selecting incorrect key derivation and/or encryption function will lead to failed password recovery. Thus with knowledge about schemes used you can significantly increase password recovery speed and without that knowledge (while trying to increase speed) you can miss valid password.
Additional note about RIPEMD key derivation. TrueCrypt encrypts boot sectors using slightly different key derivation function — it's PBKDF2/RIPEMD with 1000 iterations instead of "normal" 2000 iterations. Because of algorithm used we don't need to compute these values separately, i.e. PBKDF2/RIPEMD/1000 is a part of PBKDF2/RIPEMD/2000, so there won't be significant performance drop if you'll select RIPEMD/Boot additionally to RIPEMD/Normal.
From the other hand, having encrypted boot sector means that you also have a boot loader code, thus you can disassemble it and be absolutely sure which key derivation/encryption scheme was used.
Additional information
TrueCrypt supports key files for key derivation and there are some deprecated encryption modes other than XTS. This software does not support either of them though key files support is in nearest plans.